

Published by Springer, 2020, 332 pages, ISBN #978-3-030-60183-6. Hardback available for $84.99, eBook for $64.99. [external link].

In a world of accelerating unending change, perpetual surveillance, and increasing connectivity, conflict has become ever more complex. Wars are no longer limited to the traditional military conflict domains—land, sea, air; even space and cyber space. The new battlefield will be the cognitive domain and the new conflict a larger contest for power; a contest for cognitive superiority. Written by experts in military operations research and neuropsychology, this book introduces the concept of cognitive superiority and provides the keys to succeeding within a complex matrix where the only rules are the laws of physics, access to information, and the boundaries of cognition.
The book describes the adversarial environment and how it interacts with the ongoing, accelerating change that we are experiencing, irrespective of adversaries. It talks about the ascendant power of information access, pervasive surveillance, personalized persuasion, and emerging new forms of cognition. It profiles salient technologies and science, including persuasion science, artificial intelligence and machine learning (AI/ML), surveillance technologies, complex adaptive systems, network science, directed human modification, and biosecurity. Readers will learn about human and machine cognition, what makes it tick, and why and how we and our technologies are vulnerable.
Following in the tradition of Sun-Tsu and von Clausewitz, this book writes a new chapter in the study of warfare and strategy. It is written for those who lead, aspire to leadership, and those who teach or persuade, especially in the fields of political science, military science, computer science, and business.
The book expands on the following description of the ongoing cognified war in which we are all involved.
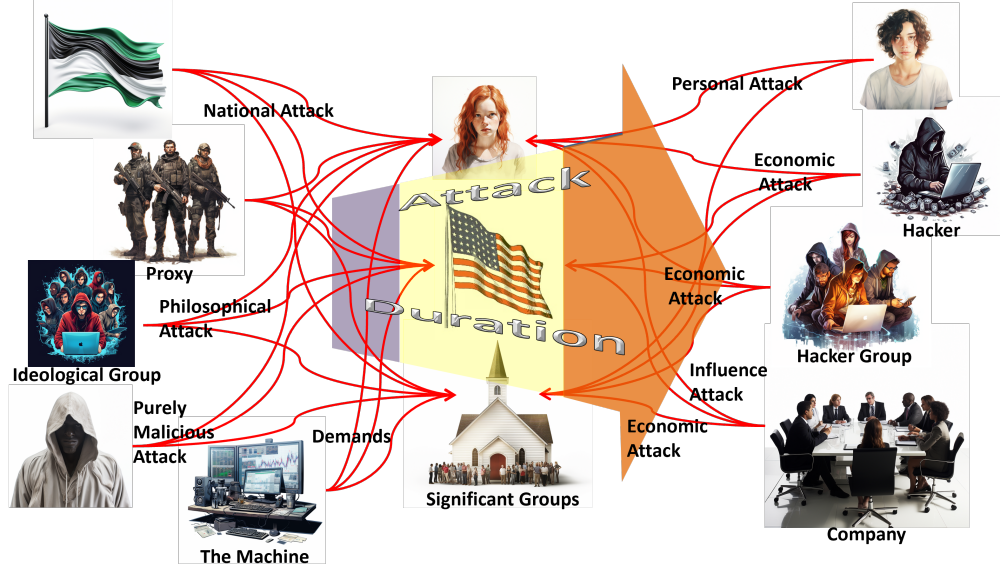 |
| Individuals include children, the elderly, ordinary adults, and adults in sensitive positions in industry and government. |
 |
| Significant groups include religious groups, political groups, small businesses and large corporations. |
 |
| The nation and its infrastructure. |
 |
| The time span runs from the nanoseconds of computer actions to the century-long war that China is waging against the US and the rest of the world. |
 |
| Nation-states. Their goals can run from changing election results to destruction of their targets. Their methods can range from social media attacks, through computer attacks, to kinetic actions. |
 |
| Proxy groups include terrorist organizations and small nation-states. They perform actions for their sponsoring nation-state that cannot be provably attributed to the nation-state. |
 |
| Ideological groups vary in size from single individuals to entire religious factions. Their goals are set by their ideology and their means generally range from computer assaults and social media influence campaigns to small-scale kinetic attacks. |
 |
| Malicious attackers have no particular goal in mind other than causing trouble or demonstrating their capabilities by whatever means possible. |
 |
| Personal attackers have a grudge against a particular person or group. Their attacks generally involve social media assassination and small-scale kinetic attacks. This category also includes "influencers" on social media who make money by reaching large audiences. |
 |
| Individual economic hackers perform attacks on computer systems to make money. |
 |
| Hacker groups also perform attacks on computer systems to make money. |
 |
| Companies seek to make money through exploiting customers' data, gaining advantages over their competition, or other economic actions. Some companies are also in the influence business. |
 |
| Machines demand time and attention from people and collect data for active attackers. |
 |
To see more about the project and to hear podcasts and see seminars
discussing the book's topics, go to the
Cognitive
Superiority Project page.
If you arrived here using a keyword shortcut, you may use your browser's "back" key to return to the keyword distribution page.
| HARTLEY
CONSULTING Solving Complex Operational and Organizational Problems Dr. Dean S. Hartley III, Principal |
|